The Ultimate SOC 2 Compliance Checklist & How to Comply
Learn what SOC 2 compliance is, why it matters, and how to achieve it. Discover key Trust Services Criteria, a step-by-step compliance checklist, and how Qovery automates and simplifies SOC 2 certification for modern cloud-native businesses.

Mélanie Dallé
May 13, 2025 · 11 min read
#Key Points
- SOC 2 is a crucial framework for protecting customer data, based on five Trust Services Criteria (Security, Availability, Processing Integrity, Confidentiality, Privacy), with Security being mandatory. It builds trust, meets obligations, and mitigates risks, essential for data-handling organizations.
- Beyond adherence, SOC 2 compliance enhances security, increases customer trust for revenue growth, improves operational efficiency, aligns with other regulations (GDPR/HIPAA), and reduces data breach risks and costs.
- The SOC 2 journey is complex, but Qovery simplifies it. It automates control enforcement via Infrastructure-as-Code, detects gaps, collects evidence, and ensures continuous compliance across clouds, significantly cutting audit time and costs.
SOC 2 (System and Organization Controls 2) is a framework developed by the American Institute of Certified Public Accountants (AICPA) to assess how organizations manage and protect customer data. Unlike other compliance standards, SOC 2 focuses on non-financial reporting controls, specifically addressing security, availability, processing integrity, confidentiality, and privacy.
There are two types of SOC 2 reports:
- SOC 2 Type 1: Evaluates the design of an organization’s controls at a single point in time. This is ideal for startups or businesses new to compliance.
- SOC 2 Type 2: Assesses the operational effectiveness of controls over a period (typically 6–12 months). Established companies often pursue this to demonstrate sustained compliance.
SOC 2 is not a one-size-fits-all certification. Organizations select the Trust Services Criteria (TSC) relevant to their operations, though Security (protecting systems from unauthorized access) is mandatory. The flexibility of SOC 2 makes it adaptable for industries like SaaS, fintech, healthcare, and cloud services, where data security and reliability are critical.
This article will explore SOC 2’s Trust Services Criteria in depth, outline a step-by-step compliance roadmap, and demonstrate how automation tools like Qovery streamline the certification process for modern cloud-native organizations.
#SOC 2 Requirements: The Trust Services Criteria (TSC)
SOC 2 compliance revolves around five Trust Services Criteria, which serve as the foundation for evaluating an organization’s controls. While Security is mandatory, the other four criteria—Availability, Processing Integrity, Confidentiality, and Privacy—are optional but often critical depending on industry and customer demands. Below is a breakdown of each criterion and its practical requirements:
#1. Security
Purpose: Protect systems and data from unauthorized access, breaches, and other security threats.
Key Controls & Examples:
- Access Controls: Implement role-based access (RBAC), multi-factor authentication (MFA), and least-privilege principles (e.g., AWS IAM policies).
- Encryption: Encrypt data at rest (e.g., AWS S3 bucket encryption) and in transit (e.g., TLS 1.2+).
- Monitoring & Logging: Deploy tools like AWS CloudTrail for audit trails and SIEM systems for real-time threat detection.
#2. Availability
Purpose: Ensure systems are operational and accessible as agreed with customers (e.g., uptime SLAs).
Key Controls & Examples:
- Disaster Recovery: Maintain backups (e.g., AWS Backup) and multi-region redundancy.
- Incident Response: Document procedures for outages (e.g., runbooks, communication protocols).
- Performance Monitoring: Use tools like AWS CloudWatch to track uptime and latency.
#3. Processing Integrity
Purpose: Guarantee data processing is complete, accurate, and timely (e.g., no errors or unauthorized alterations).
Key Controls & Examples:
- Input/Output Validation: Implement checksums or data validation rules (e.g., API request/response audits).
- Error Handling: Log and remediate processing failures (e.g., automated alerts for ETL job failures).
#4. Confidentiality
Purpose: Protect sensitive data (e.g., IP, customer PII) from unauthorized disclosure.
Key Controls & Examples:
- Data Classification: Label data by sensitivity (e.g., "public" vs. "restricted").
- NDAs & Training: Enforce confidentiality agreements and employee training programs.
#5. Privacy
Purpose: Comply with privacy commitments (e.g., GDPR, CCPA) for collecting, storing, and disposing of personal data.
Key Controls & Examples:
- Consent Management: Document user consent for data collection (e.g., cookie banners).
- Data Retention Policies: Define timelines for data deletion (e.g., automated purging after 90 days).
#Who Needs SOC 2 and Why It's Critical
SOC 2 compliance is essential for any organization that handles sensitive customer data—particularly SaaS companies, cloud service providers, fintech firms, healthcare organizations, and other technology-driven businesses. As data breaches become more frequent and regulations tighten, SOC 2 serves as a critical benchmark for proving security and operational reliability.
#Industries That Need SOC 2 Compliance
- SaaS & Cloud Providers – If your business stores or processes customer data in the cloud, SOC 2 demonstrates that you meet stringent security standards.
- Fintech & Financial Services – Companies dealing with payment processing, banking, or financial data must prove they safeguard sensitive information.
- Healthcare– Compliance ensures adherence to HIPAA and other privacy regulations while protecting patient data.
- Enterprise B2B Services – Many large enterprises require SOC 2 compliance before engaging vendors to mitigate third-party risks.
#Why SOC 2 is Non-Negotiable
- Customer Trust & Competitive Edge – A SOC 2 report reassures prospects and clients that their data is secure, often becoming a dealbreaker in sales cycles.
- Regulatory & Contractual Obligations – Many enterprise contracts and industry regulations (e.g., GDPR, CCPA) align with SOC 2 requirements.
- Risk Mitigation – Proactive security controls reduce the likelihood of breaches, which can lead to financial penalties and reputational damage.
- Investor & Partner Confidence – Startups seeking funding or partnerships use SOC 2 to validate their security posture.
#Benefits of SOC 2 Compliance
Achieving SOC 2 compliance delivers strategic advantages beyond meeting regulatory requirements. For mid-sized organizations, these benefits translate into tangible business value, operational improvements, and competitive differentiation.
#1. Enhanced Security Posture
SOC 2 forces organizations to implement and document robust security controls, including:
- Strict access management (MFA, least-privilege principles)
- Data encryption (at rest and in transit)
- Continuous monitoring (SIEM, intrusion detection)
- Incident response planning
This structured approach significantly reduces vulnerabilities and safeguards against breaches.
#2. Increased Customer Trust & Revenue Growth
- 85% of clients consider SOC 2 compliance a key factor in choosing a service provider.
Source: Deloitte Customer Satisfaction Survey
- Faster sales cycles – Eliminates 3-6 months of security questionnaires and due diligence
- Higher win rates – Differentiates against non-compliant competitors
#3. Operational Efficiency Gains
The compliance process uncovers inefficiencies in:
- Access provisioning/deprovisioning
- Change management
- Disaster recovery planning
Organizations report 30-50% faster incident response times post-compliance.
#4. Regulatory Alignment
SOC 2 maps to key frameworks:
- GDPR (Privacy requirements)
- HIPAA (Confidentiality controls)
- PCI DSS (Security standards)
This reduces duplicate efforts for organizations needing multiple certifications.
#5. Risk & Cost Reduction
- 60% of data breaches are linked to unpatched known vulnerabilities. (Source: Ponemon Institute via ServiceNow)
- $4.88 million is the global average cost of a data breach in 2024. (Source: IBM Cost of a Data Breach Report 2024)
- Reduced insurance premiums – Many cyber insurers offer discounts for SOC 2 compliance
#The SOC 2 Compliance Checklist: A Step-by-Step Guide
Achieving SOC 2 compliance requires a structured approach. Below is a detailed, phase-by-phase checklist that organizations can follow to streamline their compliance journey.
#Phase 1: Preparation & Scoping (Weeks 1–4)
Start by defining what your SOC 2 audit will cover and assessing readiness:
- Identify systems, services, and data in scope (e.g., cloud infra, third-party vendors).
- Decide whether to pursue Type I or Type II certification.
- Select which Trust Services Criteria apply beyond Security (Availability, Integrity, etc.).
- Conduct a readiness gap analysis using tools like AWS Config or platforms like Qovery.
#Phase 2: Remediation & Implementation (Weeks 5–12)
Address identified gaps with policies and controls:
- Draft key security policies (Access Control, Incident Response, Data Retention).
- Implement safeguards: MFA, data encryption (at rest and in transit), and backups.
- Set up monitoring and alerting using tools like CloudTrail or Datadog.
- Train your team on security awareness and incident protocols.
#Phase 3: Audit Execution (Weeks 13–24 for Type II)
Prepare and execute the audit:
- Collect evidence (policy docs, screenshots of controls, logs).
- Choose an AICPA-accredited firm with industry experience.
- Undergo audit: Type I checks control design; Type II tests operational effectiveness.
#Phase 4: Maintaining Compliance (Ongoing)
SOC 2 is not a one-time task:
- Use tools like Qovery for real-time monitoring and quarterly internal reviews.
- Refresh policies annually and recertify each year (for Type II).
#Key Considerations
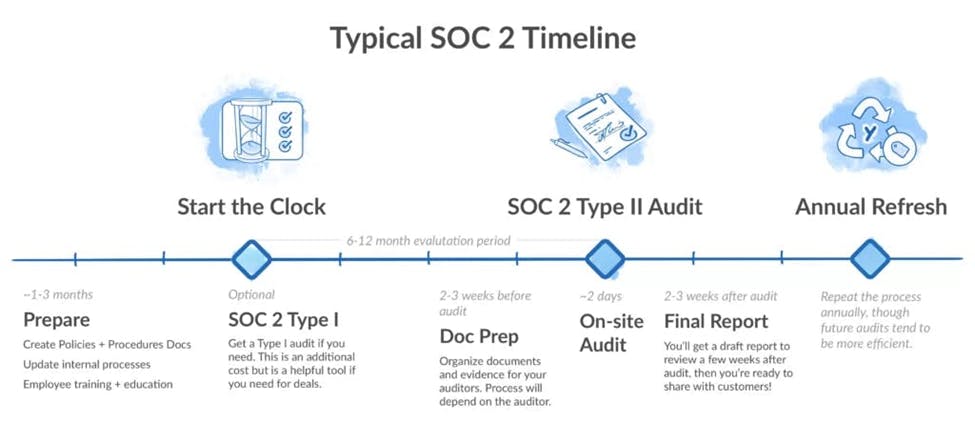
✔ Timeline:
- Type I: 2-3 months
- Type II: 6-12 months
✔ Cost:
- 20K−20K−80K depending on scope and auditor.
✔ Automation:
- Tools like Qovery reduce manual effort by auto-enforcing controls in CI/CD pipelines.
#Consequences of SOC 2 Non-Compliance: Risks and Repercussions
Failing to achieve or maintain SOC 2 compliance can have severe consequences for organizations, particularly mid-sized businesses handling sensitive customer data. Below is a detailed examination of the potential impacts:
#1. Loss of Business Opportunities
- Enterprise Contract Disqualification: 83% of enterprise buyers require SOC 2 compliance before vendor onboarding (2024 Panaseer Survey)
- Failed RFPs: Many procurement processes automatically eliminate non-compliant bidders
- Partner Rejections: Cloud marketplaces (AWS, Azure) and technology partnerships often mandate compliance
#2. Financial Penalties and Legal Exposure
- 22.7% Increase in Regulatory Fines for Non-Compliance: Organizations not adhering to regulatory requirements experienced a 22.7% increase in the share of fines exceeding $50,000 in 2024 (Source: IBM Cost of a Data Breach Report 2024 via Zscaler)
- Contractual Penalties: Many MSAs include compliance clauses with financial liabilities
- Litigation Risks: Increased vulnerability to class action lawsuits following breaches

#3. Reputational Damage
- Up to 7% increase in customer churn following a data breach: Companies that experienced a breach saw an increase of up to 7% in customer churn, equating to millions of dollars in lost revenue (Source)
- Negative Publicity: Compliance failures often become public in breach disclosures
- Review Site Impact: Security ratings (e.g., SecurityScorecard) affect sales pipelines
Recovery Timeline:
- 12-18 months to rebuild trust post-incident
- 3-5X higher customer acquisition costs during recovery
#4. Operational Disruptions
- Remediation Costs: Emergency compliance projects cost 2-3X more than proactive compliance
- Product Delays: Security rework often derails roadmaps by 6-9 months
- Team Burnout: 24/7 firefighting mode increases turnover
#5. Insurance and Financial Impacts
Cyber Insurance:
- 58% premium increases for non-compliant organizations
- 35% of claims denied for compliance violation
Valuation Impacts:
- Non-compliant SaaS companies trade at 2-3X revenue vs. 5-8X for compliant peers
- Due diligence red flags in M&A processes
#6. Security Vulnerabilities
Non-compliant organizations typically have:
- 3X more unresolved critical vulnerabilities
- 5X longer mean time to detect breaches
- 8X longer mean time to respond
Most Common Gaps Leading to Breaches:
- Inadequate access controls
- Missing encryption
- Poor audit logging
#Best SOC 2 Compliance Solutions in 2025
As compliance requirements grow more complex, DevOps automation solutions have become essential for achieving and maintaining SOC 2. Here are the top platforms that can streamline your compliance journey in 2025:
#1. Qovery
Why it Leads in 2025:
- Infrastructure-as-Code Compliance: Automatically enforces SOC 2 controls through Terraform and Kubernetes configurations
- Real-Time Gap Detection: New AI-powered scanner identifies compliance gaps in under 15 minutes
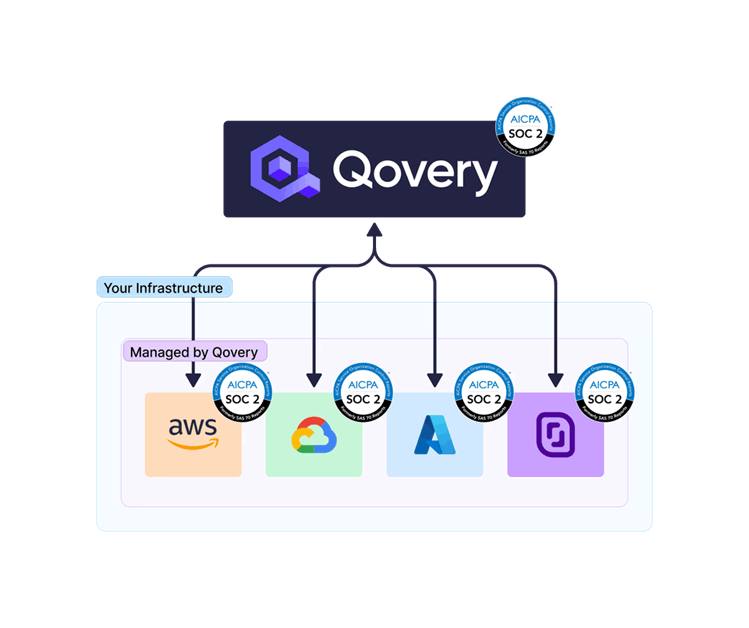
- Multi-Cloud Harmonization: Maintains consistent controls across AWS, Azure, and GCP simultaneously
2025 Enhancements:
- Automated auditor collaboration portal
- Predictive compliance risk scoring
- Built-in NIST 800-53 mapping
#2. Vanta
2025 Differentiation:
- Merged compliance workflows across 23 regulatory frameworks
- New AI evidence collection reduces manual work by 75%
- Integrated VRM module for third-party risk management
Limitations:
- Requires 3+ month implementation for complex environments
- Premium pricing (starting at approximately $10,000/year for the Essential Plan, with custom pricing for Pro and Enterprise plans ranging between $30,000–$80,000/year based on specific business needs)
#3. Drata
2025 Advantages:
- Fastest path to initial certification (average 11 weeks)
- New "Compliance Concierge" service with dedicated experts
- Automated policy generation with GPT-4 integration
Considerations:
- Less flexible for highly customized control environments
#4. SecureFrame
2025 Updates:
- Pricing starts around $7,500/year for the Fundamentals plan, with median buyer paying $20,500/year
- Visual compliance roadmap builder
- One-click auditor handoff features
#5. Thoropass
New in 2025:
- Compliance-focused investor reporting
- Embedded insurance brokerage
- SOC 2 + ISO 27001 parallel tracking
#Key Decision Factors for 2025
Implementation Speed
Automated platforms now deliver initial compliance 3–5X faster than manual approaches
AI Integration
Leading tools use AI for:
- Auto-remediation of control failures
- Smart policy generation
- Predictive risk analysis
Auditor Collaboration
Modern platforms provide:
- Direct auditor access portals
- Auto-generated audit workpapers
- Real-time compliance dashboards
Pricing Models

#Why Qovery Stands Out in 2025?
Deep DevOps Integration
- Compliance checks embedded in CI/CD pipelines
- Infrastructure drift prevention
- GitOps-compatible control management
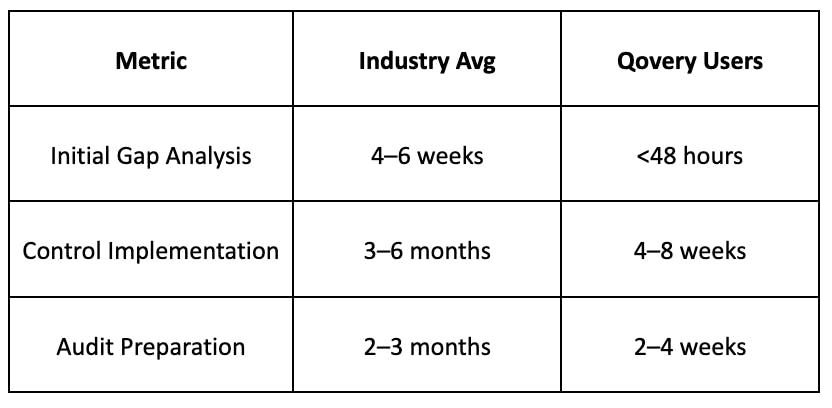
Time-to-Compliance Benchmark
Customer Results
- 92% reduction in audit preparation time
- 40% lower compliance maintenance costs
- 100% first-time audit pass rate
#How Qovery Simplifies SOC 2 Compliance
Qovery's DevOps automation tool is engineered to address SOC 2 requirements through automated, infrastructure-native controls. Here's exactly how we solve compliance challenges across each Trust Service Criterion:
Qovery helps enforce SOC 2 controls through infrastructure-native automation. Here's how it supports each Trust Services Criteria:
#1. Security
Qovery automatically provisions RBAC via Kubernetes namespaces, enforces MFA with OIDC integrations (like Okta), and applies encryption across AWS services. Real-time image scanning and penetration testing simulations enhance protection.
#2. Availability
Self-healing infrastructure replaces failing nodes quickly. Backup automation and predictive scaling reduce downtime risks.
#3. Processing Integrity
Qovery supports schema validation and deployment hash checks. Rollbacks trigger automatically on detected anomalies.
#4. Confidentiality
Its AI-assisted data classification and geo-fencing controls protect sensitive data like PII and PHI.
#5. Privacy
Qovery enables automated consent workflows and data lifecycle enforcement (including purging and cryptographic erasure).
#6. Bonus: Auditor Collaboration
Qovery includes a live evidence portal, role-based access for auditors, and built-in control mapping to SOC 2 criteria.
#Conclusion
SOC 2 compliance is no longer optional—it’s a strategic imperative for any organization handling sensitive data. By implementing robust controls and leveraging automation tools like Qovery, businesses can transform compliance from a checkbox exercise into a competitive advantage that drives customer trust, operational resilience, and revenue growth. Whether pursuing Type I or Type II certification, the journey to SOC 2 compliance strengthens your security foundation while future-proofing your organization against evolving threats and regulatory demands.
Ready to streamline your SOC 2 journey? Explore how Qovery’s DevOps automation tool can cut your compliance timeline by 80% while ensuring audit-ready controls across all Trust Services Criteria.
Your Favorite DevOps Automation Platform
Qovery is a DevOps Automation Platform Helping 200+ Organizations To Ship Faster and Eliminate DevOps Hiring Needs,
Try it out now!

Your Favorite DevOps Automation Platform
Qovery is a DevOps Automation Platform Helping 200+ Organizations To Ship Faster and Eliminate DevOps Hiring Needs,
Try it out now!


